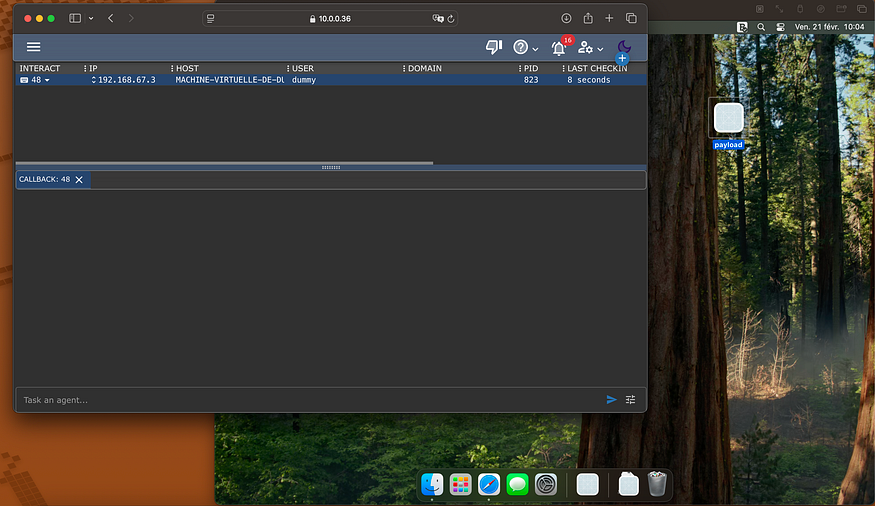
Setup and weaponize Mythic C2 using DarwinOps to target MacOS
apt install make -y
apt install git -ysudo git clone https://github.com/its-a-feature/Mythic.git
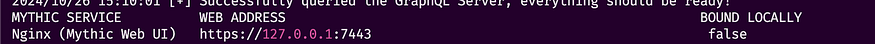
cd Mythic./install_docker_debian.sh./install_docker_kali.sh./install_docker_ubuntu.sh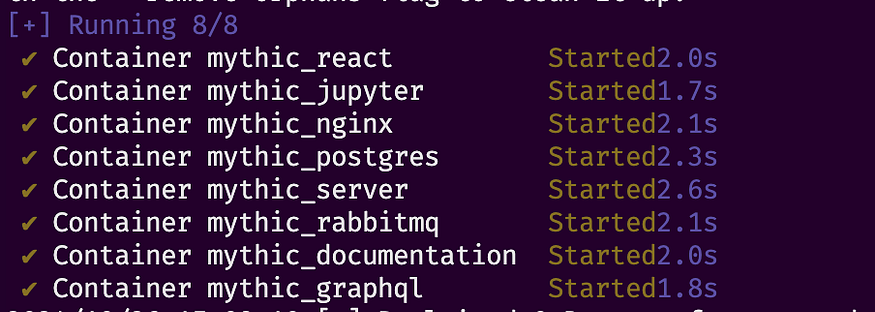

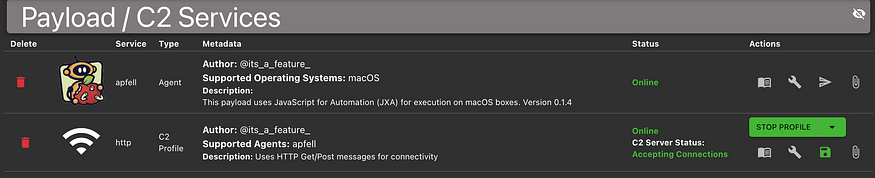
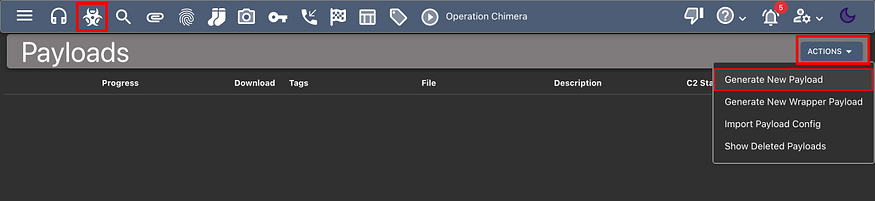
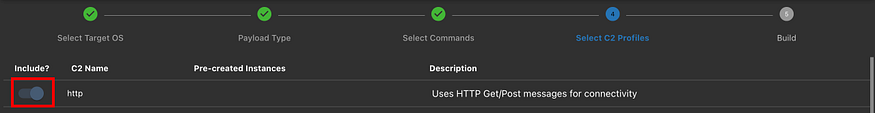
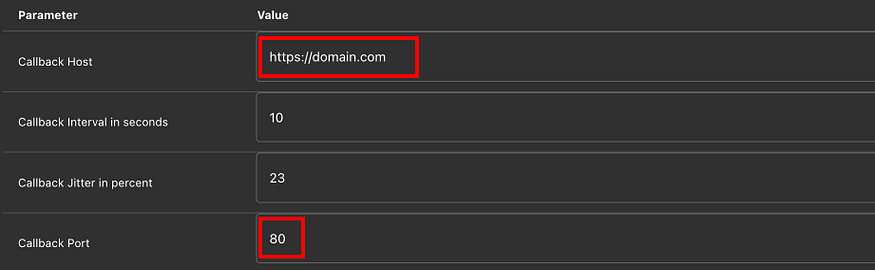
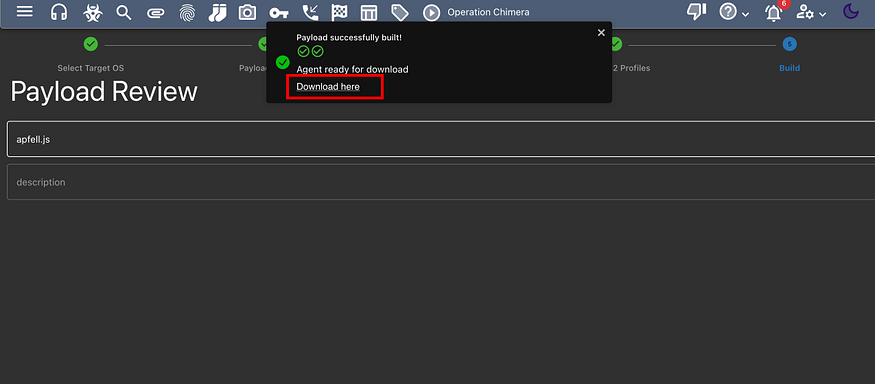
REFERENCES
Last updated