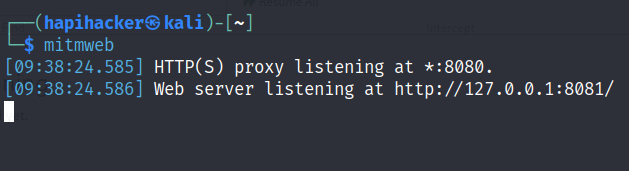
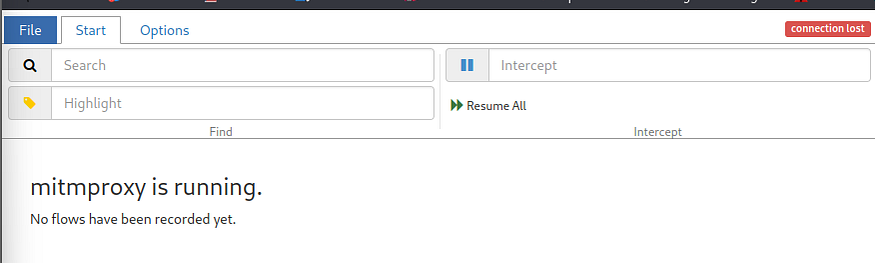
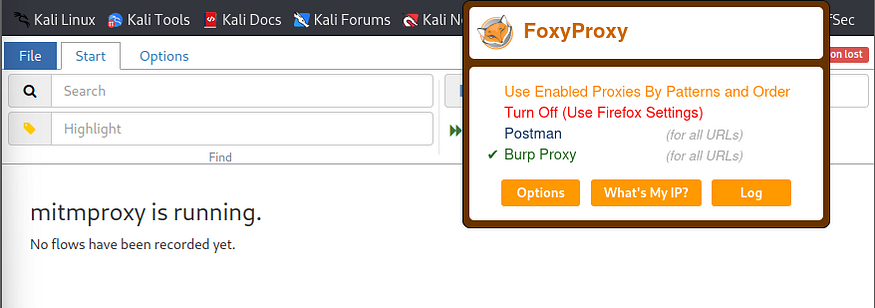
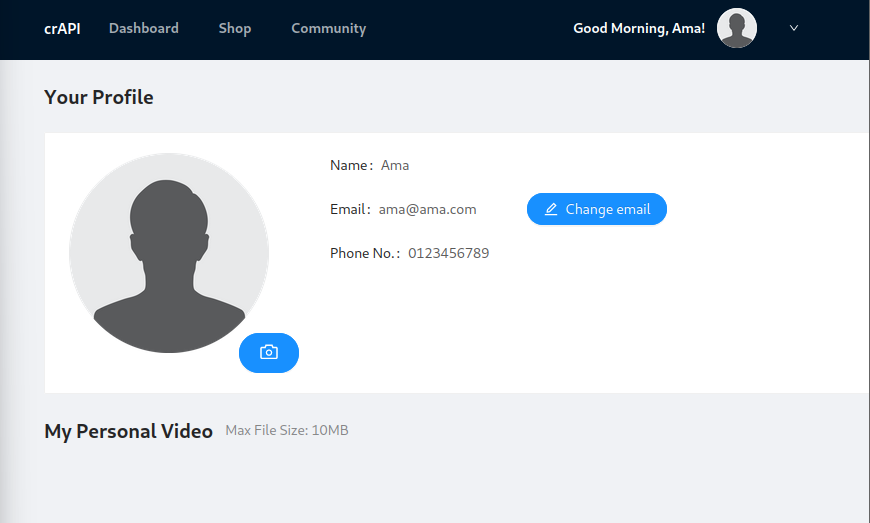
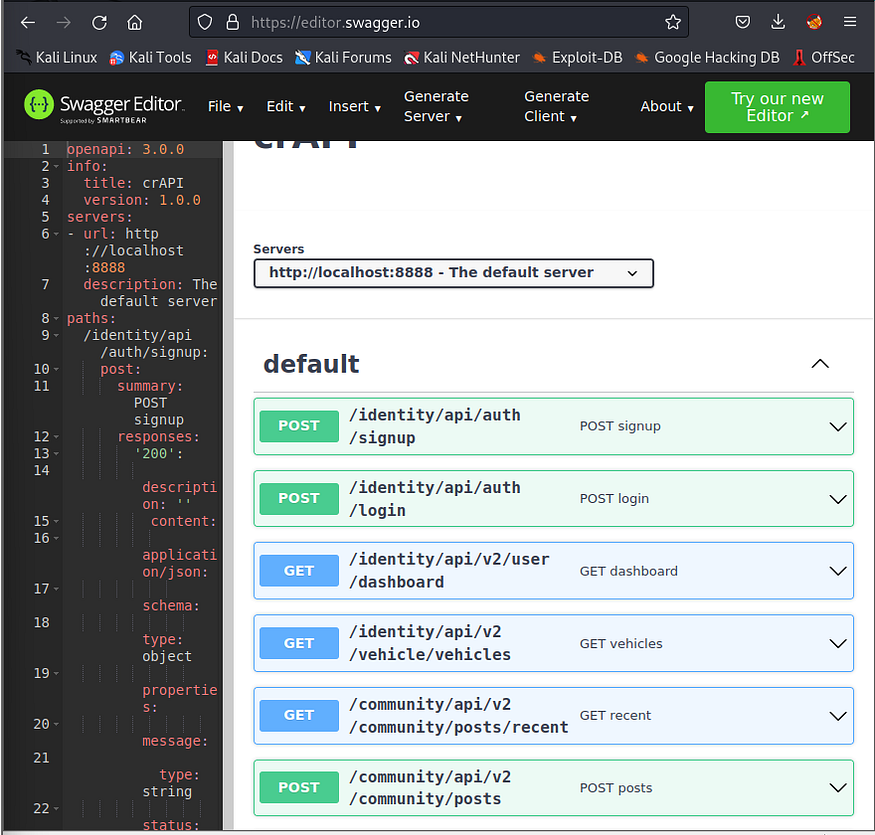
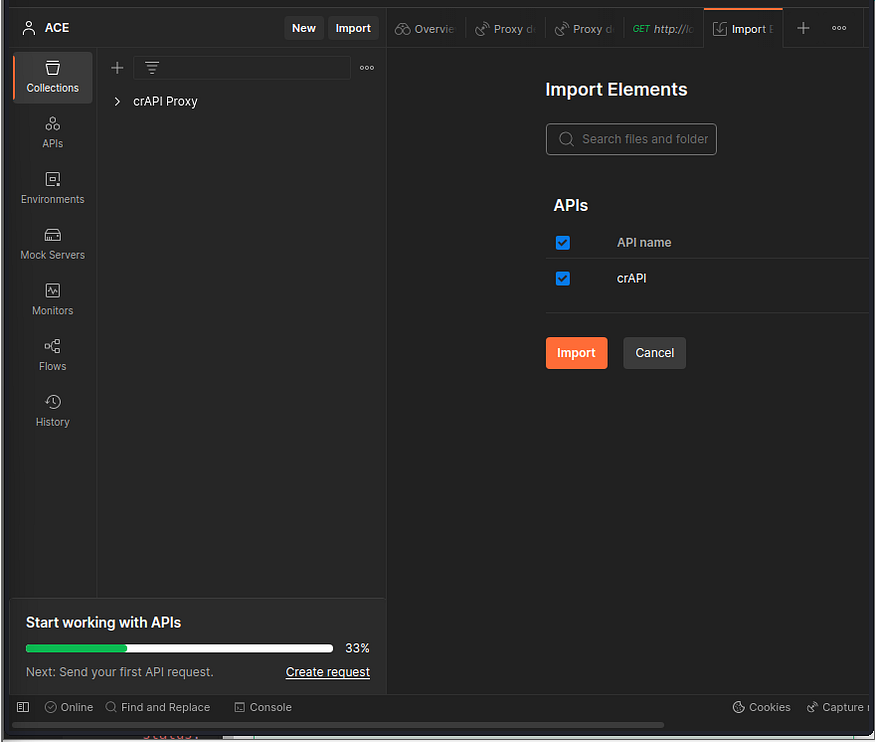
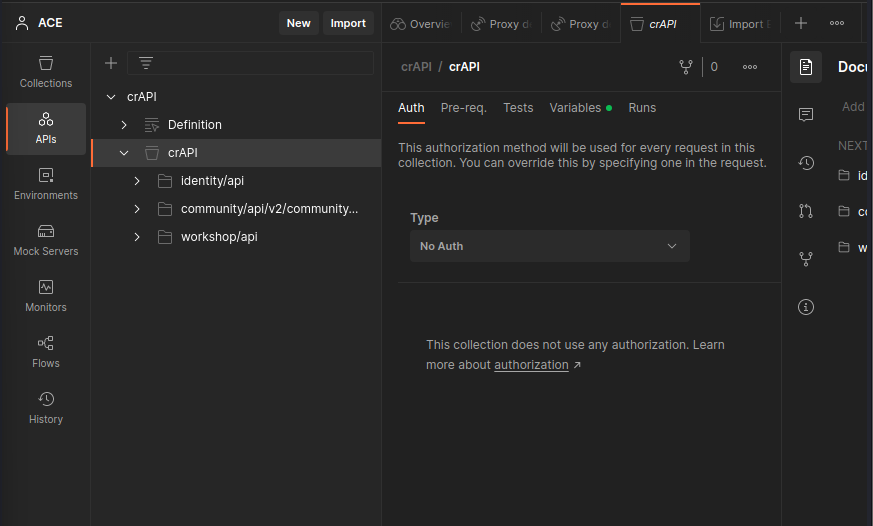
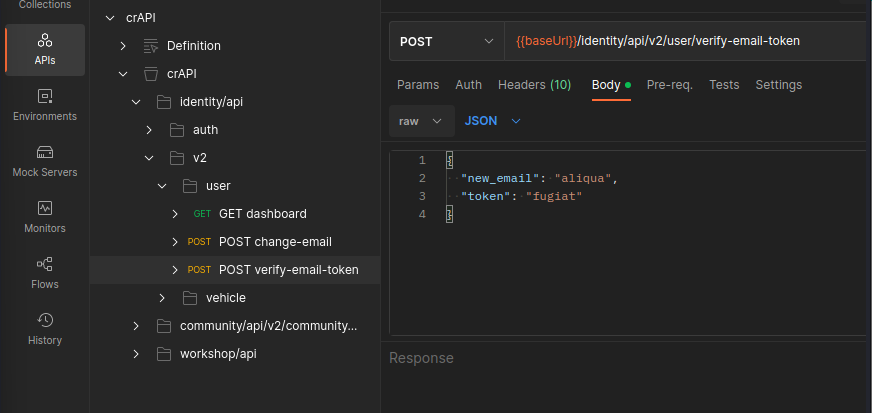
Reverse Engineer an API using MITMWEB and POSTMAN
Reverse Engineer an API using MITMWEB and POSTMAN and create a Swagger file (crAPI)
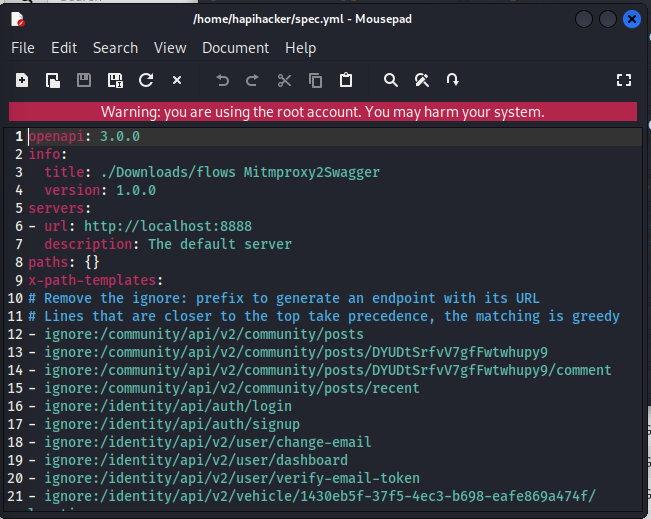
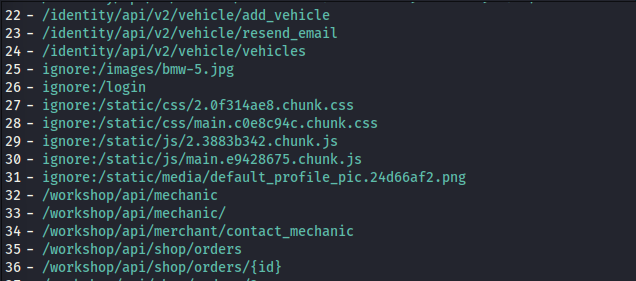
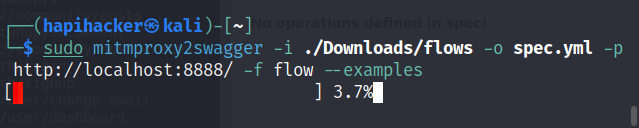
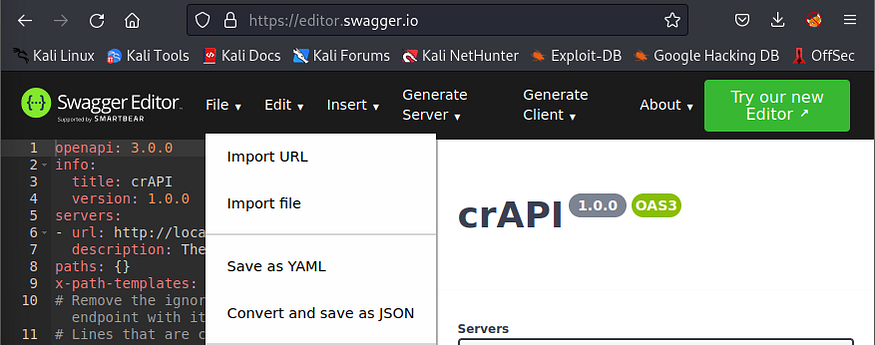
REFERENCES
Last updated